Ethical hacking and Penetration testing
Timely detection of lack of software, information systems, or certain parts of the network will always be a step ahead of the attacker. We also provide source code review services.

Our services include a wide range of penetration testing options, such as targeted volumetric attacks, dedicated software security testing, and other bespoke security evaluations.
To meet DORA requirements, we provide specialized Threat-Led Penetration Testing (TLPT) featuring comprehensive real-world exploitation scenarios. We combine in-depth attack analysis with actionable measures to reduce or eliminate identified risks. These tailored tests are designed to guarantee maximum operational resilience for your core infrastructure.
We provide ethical hacking and penetration testing services based on unique comprehensive testing methodology.
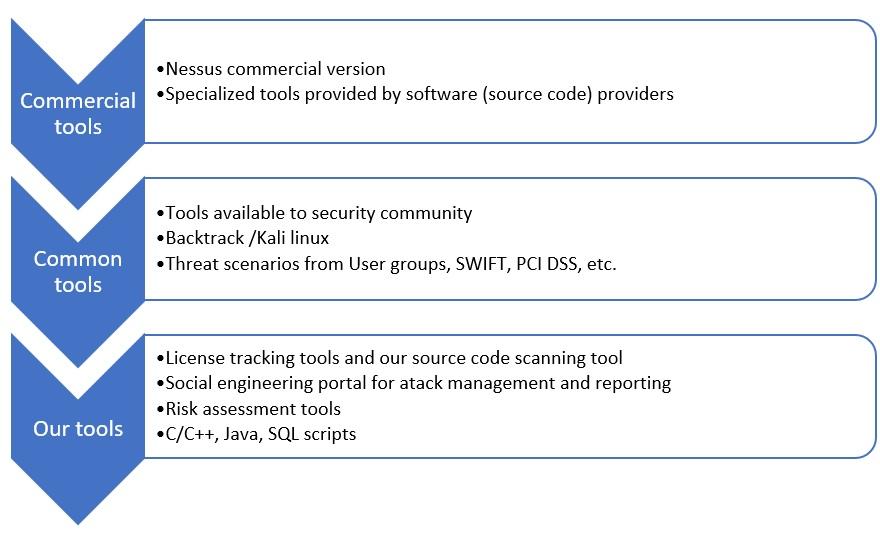
Our unique proposition: We have developed own portal and fishing attack management solution, with built-in reporting and possible exports of follow-up data.
Our unique proposition: We have developed different report export formats / software solutions to facilitate follow-up process within organization and contribute to collaboration of interesting parties.
Our unique proposition: Using recent and our specialized software solutions